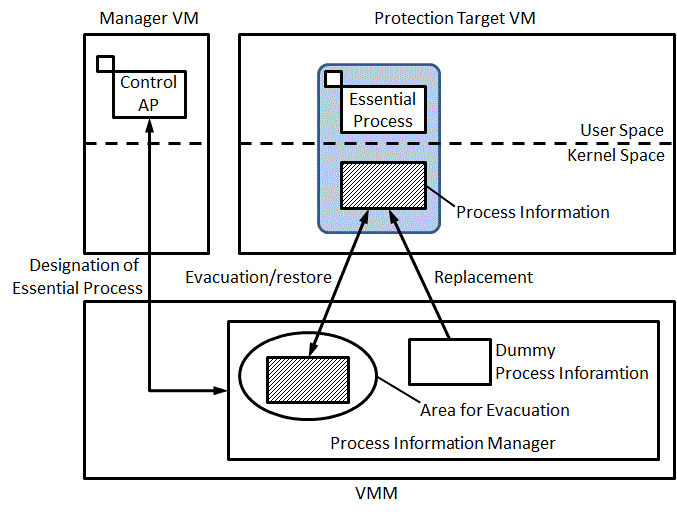
Prevention of log-tampering and loss
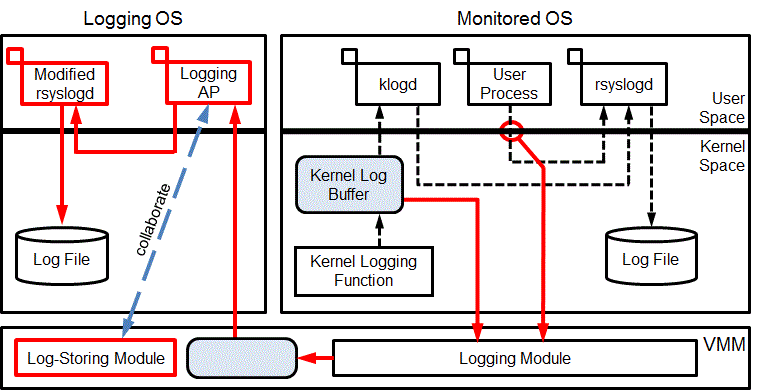
Problem with log-tampering:
Logging information about the activities that placed in a computer is essential for understanding its behavior. However, attackers can delete logs to hide evidence of their activities. Additionally, various problems may result in logs being lost.
Prevention of log-tampering:
To prevent log-tampering and loss, we utilize a virtual machine monitor. In our scheme, a virtual machine monitor detects log production inside a virtual machine and copies it to another virtual machine. With this mechanism, chances for tampering are reduced and tampering of logs after the copy becomes difficult because of virtual machine-level isolation.
Advantage:
By copying and transferring logs to another virtual machine, log-tampering after log storing becomes difficult. In addition, we can detect log-tampering not only its occurrence but also the area where the tampering occurred by comparing logs inside the monitored virtual machine and the logging virtual machine. Further, our scheme is implemented with only modifying a virtual machine monitor, therefore, no modification to software inside a virtual machine is required. This enlarges adaptability of our scheme to various operating systems.